This article describes how I set up a wireless access point that is connected to the Internet using a USB-based 3G/UMTS/HSDPA dongle.
The software and version I use is OpenWRT. For hardware, I’m using a Asus WL-500g Deluxe and WL-500g Premium V1, but any platform supported by OpenWRT should work. The 3G/UMTS/HSDPA provider is the Swedish 3 and the USB dongle is the Huawei E220.
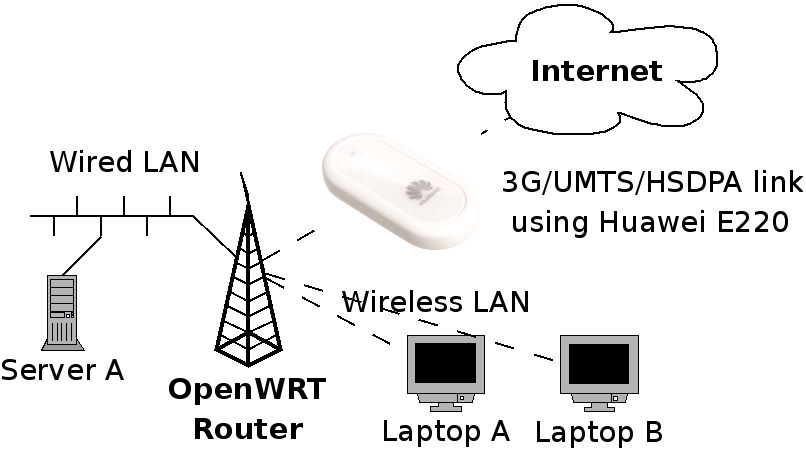
If you don’t care about the 3G setup, and care more about WDS or PSK2 encryption, you may find my home wireless network writeup more relevant. If you have an older PCMCIA based 3G/UMTS card you may want to compare this article with my summer house wireless+3g network article (however that uses older OpenWRT versions).
If you want to comment on this, please go to the blog entry.
Created by Simon Josefsson on 2009-03-05. Updated for OpenWRT 8.09.1 on 2009-06-04, OpenWRT 8.09.2 on 2010-02-03, for OpenWRT 10.03 on 2010-05-03, for OpenWRT 10.03 using the 2.6 kernel and free b43 wireless driver on 2010-12-22.
Chosing OpenWRT Image
You may build your own OpenWRT image, or you may download a pre-made image from openwrt.org.
The WL-500g Deluxe and Premium V1 devices can use both the brcm47xx and brcm-2.4 images. The brcm47xx variant uses the newer Linux 2.6.x kernel and the free wireless driver b43. The brcm-2.4 image uses the Linux 2.4 kernel and the non-free Broadcom driver, and used to be the only working image for this device. Fortunately, this has changed, and I’ll be using the brcm47xx image.
Downloading Image
To avoid building the image yourself, you may download it from openwrt.org.
$ wget --quiet http://downloads.openwrt.org/backfire/10.03/brcm47xx/openwrt-brcm47xx-squashfs.trx $ sha1sum openwrt-brcm47xx-squashfs.trx 73971dd154dfe188c73daa5e4eb19042be8930b1 openwrt-brcm47xx-squashfs.trx $
Building OpenWRT
You may skip this section if you do not want to build your own image.
Building OpenWRT is quite easy these days. I’m using Debian x86 lenny, and you will need to install gcc and other development tools. Here are the commands I used:
svn co https://svn.openwrt.org/openwrt/trunk/ mv trunk openwrt cd openwrt make menuconfig # toggle 'select all packages by default' # quit and save config make
That’s it! The complete build takes up about 2GB on my machine, and it will take quite some time to build (up to several hours).
Note that you may want to use a different branch than trunk if you are looking for something stable.
The output files will be stored into the bin/ directory.
Installing OpenWRT
There are generic Installation instructions on the OpenWRT. (Older installation instructions from the Old OpenWRT Wiki are still available.)
You’ll have to use a ethernet cable at this point. Connect it to LAN1-LAN4, not WAN. Configure your local machine on the 192.168.1.x network, for example as 192.168.1.42. The router will use 192.168.1.1. Make sure you do not have any other device using the 192.168.1.1 address and that you are on a secure network since there will be cleartext logins enabled.
On many routers, including the WL-500gD and WL-500gP, you flash an image by disconnecting power, press and hold down the reset button, and connect the power again. Wait a few seconds and the PWR led will start to blink. Release the reset button. The device will now have a tftp server running on 192.168.1.1. Ping the machine and upload the image like this.
jas@latte:~$ ping -c 3 192.168.1.1 PING 192.168.1.1 (192.168.1.1): 48 data bytes 56 bytes from 192.168.1.1: icmp_seq=0 ttl=100 time=0.545 ms 56 bytes from 192.168.1.1: icmp_seq=1 ttl=100 time=0.497 ms 56 bytes from 192.168.1.1: icmp_seq=2 ttl=100 time=0.521 ms --- 192.168.1.1 ping statistics --- 3 packets transmitted, 3 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.497/0.521/0.545/0.000 ms jas@latte:~$ tftp 192.168.1.1 tftp> trace Packet tracing on. tftp> binary tftp> put openwrt-brcm47xx-squashfs.trx sent WRQ <file=openwrt-brcm47xx-squashfs.trx, mode=octet> received ACK <block=0> sent DATA <block=1, 512 bytes> received ACK <block=1> sent DATA <block=2, 512 bytes> received ACK <block=2> ... received ACK <block=5767> sent DATA <block=5768, 512 bytes> received ACK <block=5768> sent DATA <block=5769, 0 bytes> received ACK <block=5769> Sent 2953216 bytes in 3.6 seconds tftp> quit jas@latte:~$
Wait one minute and restart the box by disconnecting and reconnecting power. Some documentations claim that the device should restart by itself but I have never seen this happen, no matter how long I wait.
Configuring OpenWRT
When the router has restarted the PWR led will lit up, and it will have a telnet server running listening on 192.168.1.1.
jas@latte:~$ telnet 192.168.1.1
Trying 192.168.1.1...
Connected to 192.168.1.1.
Escape character is '^]'.
=== IMPORTANT ============================
Use 'passwd' to set your login password
this will disable telnet and enable SSH
------------------------------------------
BusyBox v1.15.3 (2010-04-06 04:08:20 CEST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
Backfire (10.03, r20728) --------------------------
* 1/3 shot Kahlua In a shot glass, layer Kahlua
* 1/3 shot Bailey's on the bottom, then Bailey's,
* 1/3 shot Vodka then Vodka.
---------------------------------------------------
root@OpenWrt:/#
Now you can configure OpenWRT. I’ll go through each step I made, but obviously you may deviate from this description.
Set hostname
My first step was to set a hostname on the machine, use vi to edit /etc/config/system to make it read:
config system
option hostname caramel
If you prefer to cut’n'paste a command line invocation to do this, try:
root@OpenWrt:~# sed -i -e 's/OpenWrt/caramel/' /etc/config/system
Setting a hostname will help when you have multiple OpenWRT boxes running, as the command prompt will show your hostname instead of OpenWRT (after you have restarted the router).
Set IP address
If you want the device to use another IP address than 192.168.1.1 you can modify /etc/config/network, in the LAN configuration section. A quick command to do this:
root@OpenWrt:~# sed -i -e 's/192.168.1.1/192.168.1.15/' /etc/config/network
Replace telnet with SSH
As you do not want to use insecure telnet, you will need to set up ssh. You can type passwd to set a root password, and this will disable telnet. I dislike passwords, even if used over ssh, so I always set up public-key authentication and disable password authentication. For reference, there is a dropbear public key authentication howto for OpenWRT wiki page.
The command to make your ssh key authorized to login as root on the router is:
root@OpenWrt:/# echo 'PUBLICKEY' > /etc/dropbear/authorized_keys
Replace PUBLICKEY with the content of the ~/.ssh/id*.pub file on your own machine or the output from ssh-add -L if you use the SSH agent.
Disable password based login using:
root@OpenWrt:/# sed -i -e "s/'on'/'off'/" /etc/config/dropbear
Alternatively, edit /etc/config/dropbear to look like:
config dropbear
option PasswordAuth 'off'
option Port '22'
At this point, you can print the ssh host key fingerprint using:
root@OpenWrt:/# dropbearkey -y -f /etc/dropbear/dropbear_rsa_host_key Public key portion is: ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAAAgkMKE2dX9RoRKSFBwpZeTzjZI9Ec+TnAORE/L6li5trnVYv8n9drL27Oub9wrrqwhoDPtIpPaGVLyF8UWBUyXT4hrbgmyGS29UyxT6kxWf9bPLHPd1k5yadEMNhSVq6FmG7hxQH6l8igG/CmMZJYsvEPsxlEkGEedOPAL7S6IgJsHbk= root@OpenWrt Fingerprint: md5 46:16:e9:85:63:0d:56:94:32:43:fa:c4:45:d6:c4:58 root@OpenWrt:/#
To use the web interface, you may want to set a root password.
root@OpenWrt:/# passwd Changing password for root New password: Retype password: Password for root changed by root root@OpenWrt:/#
If you do not set a root password, you will need to manually disable the telnet server as follows.
root@OpenWrt:~# /etc/init.d/telnet disable
After you have made your changes, try the new configuration by rebooting both devices.
root@OpenWrt:/etc/config# reboot
After the device has restarted and the PWR led is active you should be able to login as root using SSH. Try it from your machine. The SSH fingerprint should match what was printed by dropbearkey earlier.
jas@latte:~$ ssh -l root 192.168.1.15
The authenticity of host '192.168.1.15 (192.168.1.15)' can't be established.
RSA key fingerprint is 46:16:e9:85:63:0d:56:94:32:43:fa:c4:45:d6:c4:58.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.12' (RSA) to the list of known hosts.
BusyBox v1.15.3 (2010-04-06 04:08:20 CEST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
Backfire (10.03, r20728) --------------------------
* 1/3 shot Kahlua In a shot glass, layer Kahlua
* 1/3 shot Bailey's on the bottom, then Bailey's,
* 1/3 shot Vodka then Vodka.
---------------------------------------------------
root@caramel:~#
Enabling 3G/UMTS
The USB drivers are not installed by default, so you will have to get them onto the device somehow. The simplest way to do this is if you have access to the Internet during installation. Connect the WLAN port to a network with a DHCP server and Internet connectivity. Then update the package list:
root@caramel:~# opkg update Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/Packages.gz. Inflating http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/Packages.gz. Updated list of available packages in /var/opkg-lists/packages. root@caramel:~#
You will need to re-run opkg update after every restart of the router to be able to install packages over the Internet.
A debugging tool that is useful is the lsusb tool, to inspect what kind of USB devices you have connected. Installing it and using it is optional, but can help you save time.
root@caramel:~# opkg install usbutils Installing usbutils (0.86-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/usbutils_0.86-1_brcm47xx.ipk. Installing libusb (0.1.12-2) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/libusb_0.1.12-2_brcm47xx.ipk. Installing zlib (1.2.3-5) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/zlib_1.2.3-5_brcm47xx.ipk. Configuring libusb. Configuring zlib. Configuring usbutils. Connecting to www.linux-usb.org (216.34.181.97:80) - 100% |***************************************************| 429k 00:00:00 ETA Done. root@caramel:~#
You will definitely need the kmod-usb-serial package, and one or more of the USB HCI modules: kmod-usb2 (EHCI), kmod-usb-uhci (UHCI), or kmod-usb-ohci (OHCI). For the brcm-2.4 image, the kmod-usb-uhci will normally work, but for our brcm47xx image, I’m installing them all to be ready for all kind of USB devices.
root@caramel:~# opkg install kmod-usb-serial kmod-usb2 kmod-usb-uhci kmod-usb-ohci Installing kmod-usb-serial (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-usb-serial_2.6.32.10-1_brcm47xx.ipk. Installing kmod-usb-core (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-usb-core_2.6.32.10-1_brcm47xx.ipk. Installing kmod-nls-base (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-nls-base_2.6.32.10-1_brcm47xx.ipk. Installing kmod-usb2 (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-usb2_2.6.32.10-1_brcm47xx.ipk. Installing kmod-usb-uhci (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-usb-uhci_2.6.32.10-1_brcm47xx.ipk. Installing kmod-usb-ohci (2.6.32.10-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/kmod-usb-ohci_2.6.32.10-1_brcm47xx.ipk. Configuring kmod-nls-base. Configuring kmod-usb-core. Configuring kmod-usb-ohci. Configuring kmod-usb2. Configuring kmod-usb-serial. Configuring kmod-usb-uhci. root@caramel:~#
At this point I reboot the device to have USB be initialized properly. For me USB did not initialize correctly without a reboot
If everything works, you should see something like the output below. (If you didn’t install the lsusb tool, try cat /proc/bus/usb/devices instead.)
root@caramel:~# lsusb Bus 004 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub Bus 003 Device 002: ID 12d1:1003 Huawei Technologies Co., Ltd. E220 HSDPA Modem / E230/E270 HSDPA/HSUPA Modem Bus 003 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub Bus 002 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub root@caramel:~#
You will likely need to configure the usbserial driver to claim the serial device and then reboot the router. Here is how to do it:
root@caramel:~# cat>/etc/modules.d/60-usb-serial usbserial vendor=0x12d1 product=0x1003 maxSize=4096 root@caramel:~# reboot
If you are using some other device than the E220 you will need to modify the USB vendor/product IDs as appropriate.
Reboot the box, and if you are lucky you should see something like this in the kernel log:
USB Serial support registered for generic usbserial_generic 3-1:1.0: generic converter detected usb 3-1: generic converter now attached to ttyUSB0 usbserial_generic 3-1:1.1: generic converter detected usb 3-1: generic converter now attached to ttyUSB1 usbserial_generic 3-1:1.2: generic converter detected usb 3-1: generic converter now attached to ttyUSB2 usbcore: registered new interface driver usbserial_generic usbserial: USB Serial Driver core
If that doesn’t happen, you may need a tool that nudges the modem into revealing its serial ports (by default it is a storage device). I believe the E220 will reveal its serial ports automatically after a few minutes, so if you have the patience to wait you should not need this step. If you decide to speed things up, the package huaweiaktbbo helps here. Don’t forget to run opkg update first.
root@caramel:~# opkg install huaweiaktbbo Installing huaweiaktbbo (1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/huaweiaktbbo_1_brcm47xx.ipk. Configuring huaweiaktbbo. root@caramel:~#
The tool is used as follows.
root@caramel:~# huaweiAktBbo Searching modem...found supported modem! Modem poked! root@caramel:~#
To run this command automatically after each reboot, you can add a small init.d script as follows (instead of ^D press Control-D):
root@caramel:~# cat>/etc/init.d/huaweiAktBbo
#!/bin/sh /etc/rc.common
# Written by Simon Josefsson 2009-03-05. Released into the public domain.
START=70
start() {
huaweiAktBbo
}
^D
root@caramel:~# chmod +x /etc/init.d/huaweiAktBbo
root@caramel:~# /etc/init.d/huaweiAktBbo enable
The next step is to get dial-up PPP working. The comgt package contains several useful 3G/UMTS scripts.
root@caramel:~# opkg install comgt Installing comgt (0.32-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/comgt_0.32-1_brcm47xx.ipk. Installing chat (2.4.4-5) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/chat_2.4.4-5_brcm47xx.ipk. Configuring chat. Configuring comgt. root@caramel:~#
The next step is to configure a network interface for the 3G/UMTS/HSDPA interface. I ended up modifying the wan section of /etc/config/network to read as follows:
#### WAN configuration
config interface wan
option ifname ppp0
option proto 3g
option device /dev/usb/tts/0
option apn bredband.tre.se
option pincode 1234
You will need to modify the apn and pincode settings as appropriate.
Now the command ifup wan should work, and will print something like this:
root@caramel:~# ifup wan Trying to set PIN PIN set successfully root@caramel:~#
Use logread to inspect the pppd debug messages, which could look like this:
Dec 22 22:01:50 kladdkaka daemon.notice pppd[1293]: pppd 2.4.4 started by root, uid 0 Dec 22 22:01:51 kladdkaka local2.info chat[1300]: abort on (BUSY) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: abort on (NO CARRIER) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: abort on (ERROR) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: report (CONNECT) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: timeout set to 10 seconds Dec 22 22:01:51 kladdkaka local2.info chat[1300]: send (AT&F^M) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: expect (OK) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: AT&F^M^M Dec 22 22:01:51 kladdkaka local2.info chat[1300]: OK Dec 22 22:01:51 kladdkaka local2.info chat[1300]: -- got it Dec 22 22:01:51 kladdkaka local2.info chat[1300]: send (ATE1^M) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: expect (OK) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: ^M Dec 22 22:01:51 kladdkaka local2.info chat[1300]: ATE1^M^M Dec 22 22:01:51 kladdkaka local2.info chat[1300]: OK Dec 22 22:01:51 kladdkaka local2.info chat[1300]: -- got it Dec 22 22:01:51 kladdkaka local2.info chat[1300]: send (AT+CGDCONT=1,"IP","bredband.tre.se"^M) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: timeout set to 30 seconds Dec 22 22:01:51 kladdkaka local2.info chat[1300]: expect (OK) Dec 22 22:01:51 kladdkaka local2.info chat[1300]: ^M Dec 22 22:01:51 kladdkaka local2.info chat[1300]: AT+CGDCONT=1,"IP","bredband.tre.se"^M^M Dec 22 22:01:51 kladdkaka local2.info chat[1300]: OK Dec 22 22:01:51 kladdkaka local2.info chat[1300]: -- got it Dec 22 22:01:51 kladdkaka local2.info chat[1300]: send (ATD*99***1#^M) Dec 22 22:01:52 kladdkaka local2.info chat[1300]: expect (CONNECT) Dec 22 22:01:52 kladdkaka local2.info chat[1300]: ^M Dec 22 22:01:52 kladdkaka local2.info chat[1300]: ATD*99***1#^M^M Dec 22 22:01:52 kladdkaka local2.info chat[1300]: CONNECT Dec 22 22:01:52 kladdkaka local2.info chat[1300]: -- got it Dec 22 22:01:52 kladdkaka local2.info chat[1300]: send ( ^M) Dec 22 22:01:52 kladdkaka daemon.info pppd[1293]: Serial connection established. Dec 22 22:01:52 kladdkaka daemon.info pppd[1293]: Using interface ppp0 Dec 22 22:01:52 kladdkaka daemon.notice pppd[1293]: Connect: ppp0 <--> /dev/ttyUSB0 Dec 22 22:01:55 kladdkaka daemon.warn pppd[1293]: Could not determine remote IP address: defaulting to 10.64.64.64 Dec 22 22:01:55 kladdkaka daemon.info dnsmasq[1042]: reading /tmp/resolv.conf.auto Dec 22 22:01:55 kladdkaka daemon.info dnsmasq[1042]: using nameserver 80.251.201.178#53 Dec 22 22:01:55 kladdkaka daemon.info dnsmasq[1042]: using nameserver 80.251.201.177#53 Dec 22 22:01:55 kladdkaka daemon.info dnsmasq[1042]: using local addresses only for domain lan Dec 22 22:01:55 kladdkaka daemon.notice pppd[1293]: replacing old default route to eth0.1 [192.168.1.15] Dec 22 22:01:55 kladdkaka daemon.notice pppd[1293]: local IP address 109.58.87.227 Dec 22 22:01:55 kladdkaka daemon.notice pppd[1293]: remote IP address 10.64.64.64 Dec 22 22:01:55 kladdkaka daemon.notice pppd[1293]: primary DNS address 80.251.201.177 Dec 22 22:01:55 kladdkaka daemon.notice pppd[1293]: secondary DNS address 80.251.201.178
The speed I got when downloading a Debian CD image is around 235kb/s (1880Mbps) which is sufficiently fast that I haven’t looked into ways to increase speed.
To make the interface come up automatically on startup, you can add a small init.d script like this (replace ^D with Control-D as before):
root@caramel:/etc/rc.d# cat>/etc/init.d/wan
#!/bin/sh /etc/rc.common
# Written by Simon Josefsson 2009-03-05. Released into the public domain.
START=90
start() {
ifup wan
}
^D
root@caramel:/etc/rc.d# chmod +x /etc/init.d/wan
root@caramel:/etc/rc.d# /etc/init.d/wan enable
root@caramel:/etc/rc.d#
Non-WAN configuration
If you for some reason wish to keep the ethernet WAN port on the box as the "real" Internet connection — perhaps to use the 3G part only as a backup Internet connection in case the other one goes down? — instead of replacing the existing WAN section in the file, add a new section:
#### 3G/UMTS configuration
config interface ppp0
option ifname ppp0
option proto 3g
option device /dev/usb/tts/0
option apn bredband.tre.se
option pincode 1234
You need to use ifup ppp0 insetad of ifup wan now.
TODO: There seems to be some bad firewall interaction with this approach, needs to be investigated (workaround is to keep two /etc/config/network files, one for WAN over ethernet and one for WAN over 3G).
Setup wireless
A natural next step is to configure wireless, but this writeup is not about this. There are many documents out there to help you. I have written about my home wireless network setup which may be of interest.
Remote logins
I want to be able to access the router remotely and it doesn’t have a static IP address. The first step is to make sure I can find the IP address of the router remotely. Installing and using ez-ipupdate is easy.
root@caramel:/# opkg install ez-ipupdate Installing ez-ipupdate (3.0.11b8-4) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm47xx/packages/ez-ipupdate_3.0.11b8-4_brcm47xx.ipk. Configuring ez-ipupdate. root@caramel:/#
I’m using DynDNS which doesn’t cost anything and have been working without problems for me so far. My /etc/config/ddns file looks like:
config ddns
option enabled 1
option interface wan
option program ez-ipupdate
option service dyndns
option username USERNAME
option password PASSWORD
option hostname HOSTNAME
# config ddns
# option interface wan
# option program ez-ipupdate
# option config /etc/ez-ipupdate.conf
Replace USERNAME and PASSWORD with your DynDNS account information. Replace HOSTNAME with the hostname you’ve registered. Note that you must change the value for "enabled" from 0 to 1.
You also need to open up the firewall to allow incoming connections on port 22 (the ssh port), which can be done using a small init.d script like this:
root@caramel:~# cat>/etc/init.d/open-wan-ssh-port
#!/bin/sh /etc/rc.common
# Written by Simon Josefsson 2009-03-05. Released into the public domain.
START=90
start() {
iptables --append input_wan --protocol tcp --dport 22 --jump ACCEPT
}
^D
root@caramel:~# chmod +x /etc/init.d/open-wan-ssh-port
root@caramel:~# /etc/init.d/open-wan-ssh-port enable
Additional software
You can use opkg to install additional tools easily. First run opkg update to update the package list:
root@caramel:~# opkg update Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/Packages.gz. Inflating http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/Packages.gz. Updated list of available packages in /var/opkg-lists/packages. root@caramel:~#
Use opkg list to list all available packages.
Useful tools to install on a typical router includes avahi-daemon, miniupnpd, and openntpd.
The clock will typically be way off unless you set it. Install a NTP client to automate keeping the clock correct. (The package openntpd also works but takes more space.)
root@caramel:~# opkg install luci-app-ntpc Installing luci-app-ntpc (0.9.0-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/luci-app-ntpc_0.9.0-1_brcm-2.4.ipk. Installing ntpclient (2007_365-4) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/ntpclient_2007_365-4_brcm-2.4.ipk. Configuring ntpclient. Configuring luci-app-ntpc. root@caramel:~#
Avahi allows DNS based service discovery, which is relevant on both primary and repeater routers. Install and enable as follows:
root@caramel:~# opkg install avahi-daemon Installing avahi-daemon (0.6.25-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/avahi-daemon_0.6.25-1_brcm-2.4.ipk. Installing libavahi (0.6.25-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/libavahi_0.6.25-1_brcm-2.4.ipk. Installing libdaemon (0.14-2) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/libdaemon_0.14-2_brcm-2.4.ipk. Installing libpthread (0.9.30.1-42) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/libpthread_0.9.30.1-42_brcm-2.4.ipk. Installing librt (0.9.30.1-42) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/librt_0.9.30.1-42_brcm-2.4.ipk. Installing libgdbm (1.8.3-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/libgdbm_1.8.3-1_brcm-2.4.ipk. Installing libexpat (2.0.1-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/libexpat_2.0.1-1_brcm-2.4.ipk. Configuring librt. Configuring libpthread. Configuring libdaemon. Configuring libgdbm. Configuring libavahi. Configuring libexpat. Configuring avahi-daemon. root@caramel:~# /etc/init.d/avahi-daemon enable root@caramel:~# /etc/init.d/avahi-daemon start root@caramel:~#
You should now be able to login to your router using ssh -l root caramel.local (replace caramel with the name of your router).
Bittorrent clients, for example, can use UPnP to open up ports in the firewall. For this to work, install a UPnP server on your primary router (it makes no sense to install it on the repeaters):
root@caramel:~# opkg install miniupnpd luci-app-upnp Installing miniupnpd (1.4-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/miniupnpd_1.4-1_brcm-2.4.ipk. Installing luci-app-upnp (0.9.0-1) to root... Downloading http://downloads.openwrt.org/backfire/10.03/brcm-2.4/packages/luci-app-upnp_0.9.0-1_brcm-2.4.ipk. Configuring miniupnpd. Configuring luci-app-upnp. root@caramel:~# /etc/init.d/miniupnpd enable root@caramel:~# /etc/init.d/miniupnpd start root@caramel:~#
The End
This work is licensed under a Creative Commons Attribution-Share Alike 3.0 Unported License.
